Enterprise AI Security in Salesforce - Complete Implementation Guide
What?
A practical guide to implementing AI securely in your enterprise, focusing on data protection, compliance, and risk management.
Who?
Security teams, Compliance officers, IT leaders, Admins, and Business leaders concerned about risk of AI in Salesforce.
Why?
To implement AI confidently without compromising sensitive information.
→ Keep data safe. Follow the rules. Build trust.
Introduction
As businesses adopt AI, an important question arises: How can we leverage its potential while safeguarding our data? This goes beyond merely adhering to regulations – it involves fostering trust with your customers and upholding your organization's integrity in a world shaped by AI.
Every organization is exploring AI capabilities; the difference between success and failure often lies not in the technology itself but in how securely you implement it.
Three Key Areas of Safe AI
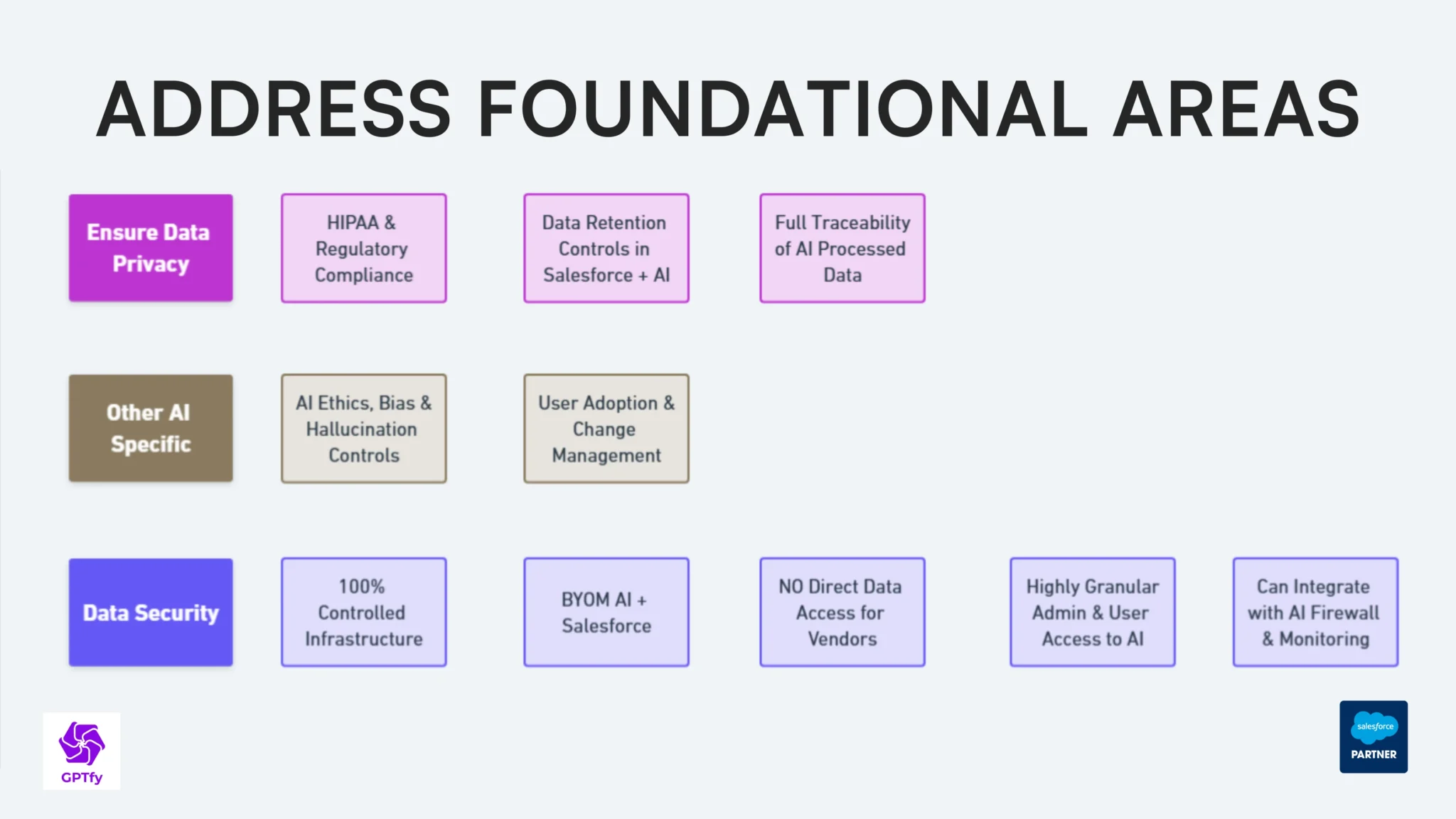
1. Data Privacy and Protection
The key to successfully implementing AI lies in strong data privacy measures. Consider it like constructing a house; a sturdy foundation is essential before incorporating elegant features.
Before diving into AI implementation, you need a clear picture of your data landscape. Just as a map helps navigate unfamiliar territory, a data inventory helps you understand what needs protection:
- Create a comprehensive inventory of sensitive data types
- Map data flows across your systems
- Identify high-risk information areas
- Document applicable privacy regulations
For example, a healthcare provider might need to track patient IDs, diagnosis codes, and treatment information, while a financial services company focuses on account numbers and transaction details.
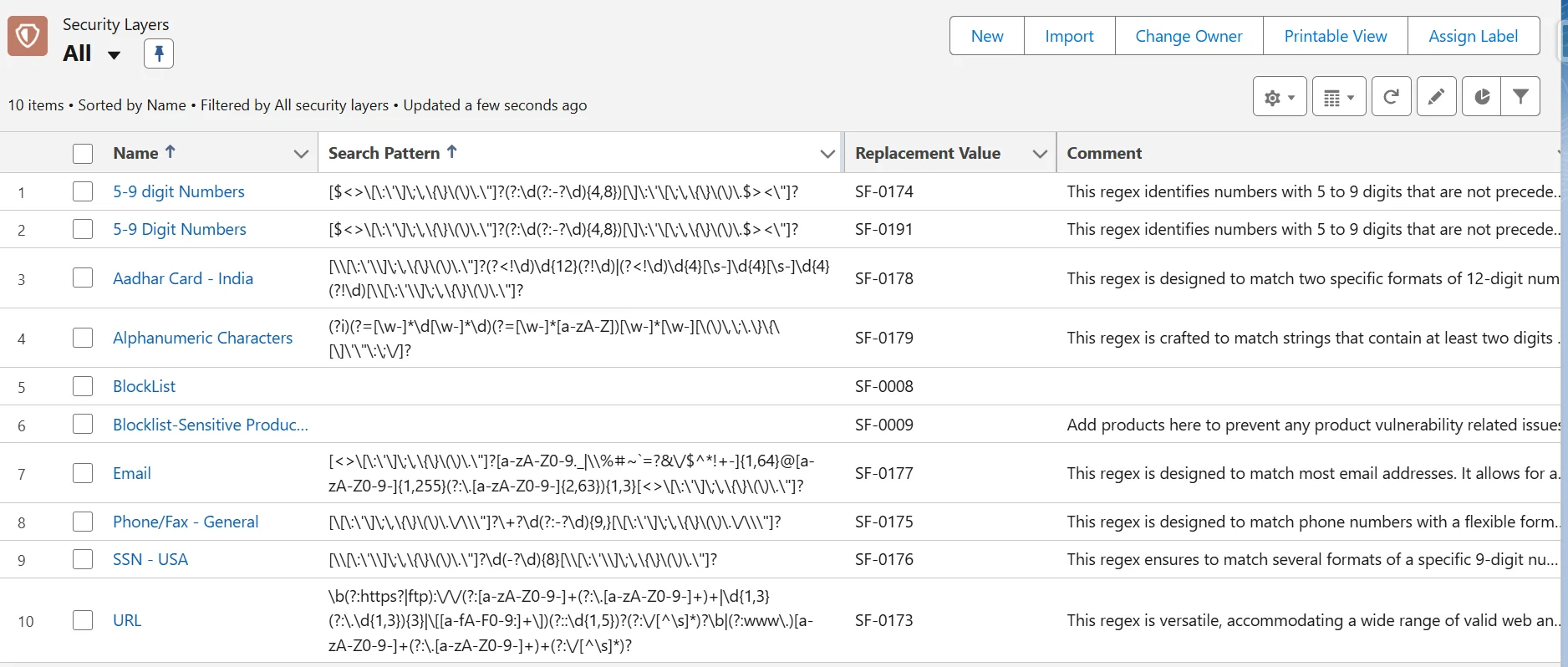
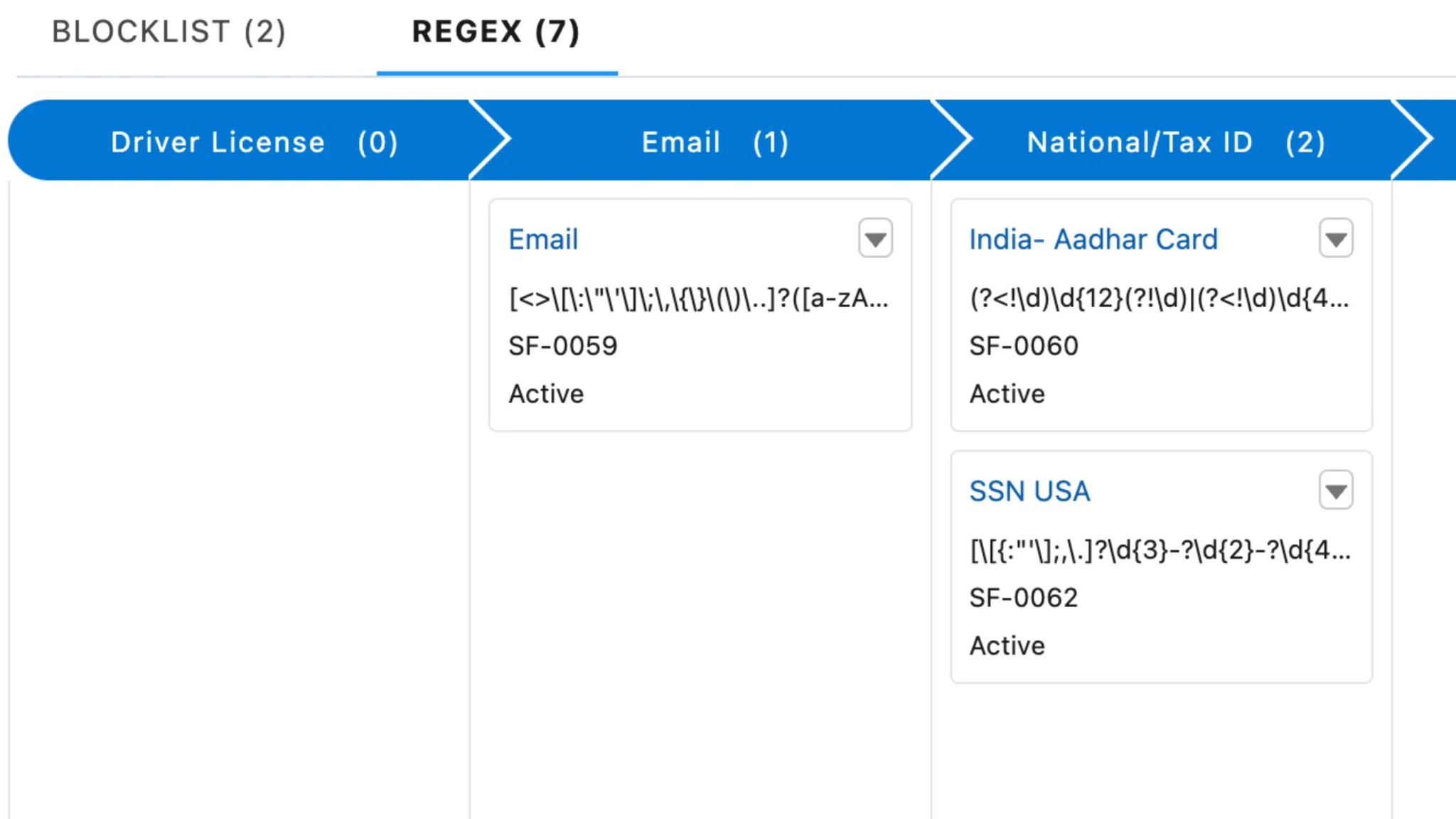
Automated Data Protection
Modern AI systems need robust, automated protection mechanisms. It's like having an intelligent security system that knows exactly what to protect:
- Screen for personal information (SSNs, credit card numbers)
- Protect health data (HIPAA compliance)
- Secure business details (account balances, contract terms)
When a customer service representative pulls up a record, the system automatically masks sensitive fields before sending data to the AI model, ensuring compliance while maintaining functionality.
2. Control Access and Use
Setting Up User Rules
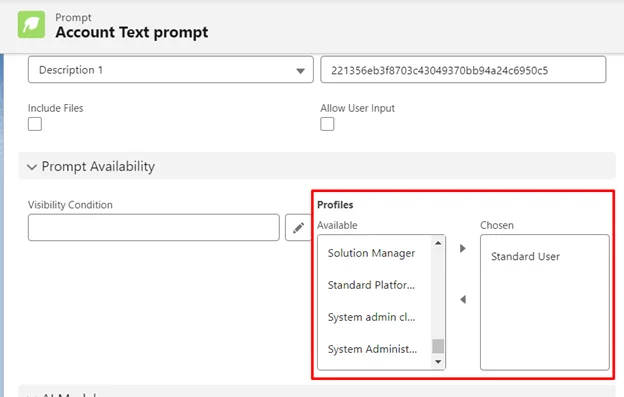
Configuration page showing the Prompt Availability settings with Standard User profile selected to restrict prompt access to specific users.
Think of access control like a building's security system – different people need different levels of access. Prompt Builder helps you configure these controls:
- Control by job role
- Set manager access levels
- Define team member permissions
- Establish admin rights
- Add business rules
- Limit by department
- Set time restrictions
- Define usage conditions
Monitoring System Use
Just like a security camera system, you need real-time visibility:
- Watch active usage patterns
- Track unusual activities
- Monitor system health
- Measure response times
3. AI Behavior Control
Setting Response Rules
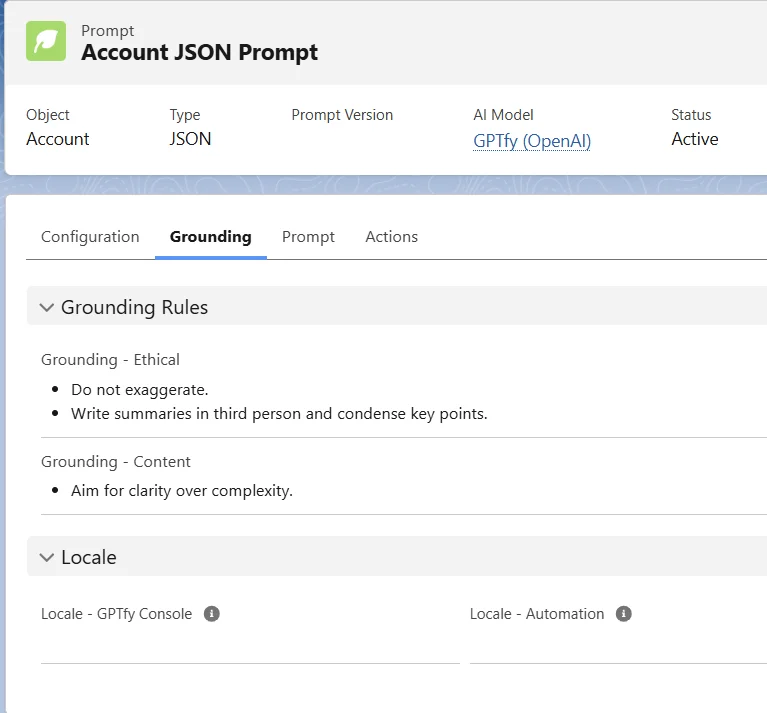
Consider this your AI's playbook for interacting with users:
- Control AI tone and professionalism
- Guide response format and detail level
- Implement safety checks and verification
Quality Control
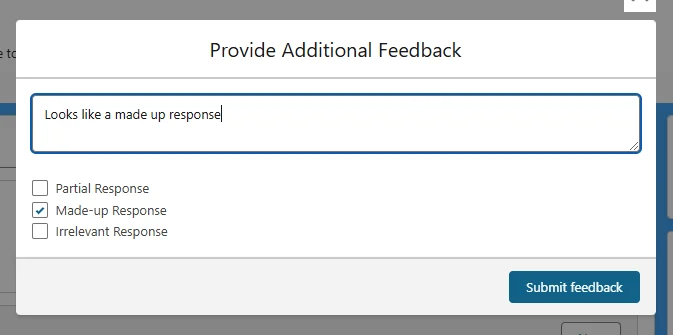
Think of this as your AI's continuous improvement program:
- Regular response reviews
- User feedback collection
- Systematic improvements
- Best practice sharing
Implementation Plan
First 30 Days: Building the Foundation
- Set up basic data protection
- Implement initial logging
- Define core access rules
- Train pilot users
Days 31–60: Strengthening Controls
- Enhance data masking
- Improve tracking systems
- Refine access controls
- Deploy monitoring
Days 61–90: Fine-Tuning
- Optimize rules based on learning
- Add advanced features
- Expand monitoring capabilities
- Share success stories
Next Steps
-
Assess Your Current State
- Document sensitive data types
- Review existing security measures
- Identify immediate risks
-
Build Your Protection Framework
- Design data masking rules
- Create access control plans
- Develop monitoring strategies
- Start Small, Scale Smart
- Begin with a pilot group
- Gather feedback and adjust
- Expand gradually
Conclusion
Implementing secure AI isn't just about following a checklist – it's about creating a sustainable, secure environment where AI can thrive while protecting your organization's most valuable assets: its data and reputation.
Remember: Security in AI is not a destination but a journey. Start with strong foundations, build incrementally, and always stay vigilant.
Ready to implement secure AI in your Salesforce enterprise? Book a demo to see GPTfy's multi-layered security features in action.
Want to learn more?
View the Datasheet
Get the full product overview with architecture details, security specs, and pricing — with a built-in print option.
Watch a 2-Minute Demo
See GPTfy in action inside Salesforce - from prompt configuration to AI-generated output in real time.
Ready to see it with your data? Book a Demo
